A good deal of recent content from analysts, vendors, and IT industry experts makes a strong case that most users and digital assets lie outside the physical and logical boundaries of the organization.
Although the validity of this assertion cannot be confirmed in absolute terms, it is fair to recognize that the COVID-19 pandemic has led to a hybrid work model and that the adoption of the cloud and mobility are growing rapidly throughout the world, due to the of digital transformation.
It is more realistic and safer to say, therefore, that sooner rather than later a significant volume of applications, data, and devices will be housed in hybrid multi cloud environments (“hybrid multi cloud”).
Traditional security architectures, based on establishing a network perimeter with stacks of devices, simply cannot cope with this new technology normal where most of the associated risks are external.
A distributed environment characterized by the presence of resources everywhere, accessible from anywhere, also unequivocally requires a distributed protection model, an architecture capable of placing controls exactly in the place, time, and dose needed.
Manuel Aceves Mercenario, Innovation Director of Tautenet, will talk about this in his talk The day cybersecurity became ubiquitous at the 7th America Digital Latin American Congress of Business & Technology 2022.
Manuel Aceves M. was the partner responsible for Andersen and Deloitte’s information security practices for Latin America. For HSBC he served as regional CISO for this same territory.
He was also Global Vice President and member of the Information Systems Audit and Control Association (ISACA) Board of Directors, Security Management Committee, Professional Standards Committee and the Cybersecurity Advisory Task Force. Today, he is passionately dedicated to innovation in Cybersecurity.

A new concept
This architectural model is called Cybersecurity Mesh, it was just coined by Gartner Inc. in March 2021 and today represents one of the most visible technological trends within business ecosystems.
As a metaphor, the term invokes the idea of a ubiquitous mesh, always present and close, that simultaneously envelops and protects our users and IT assets, regardless of their location.
In practice, it is closer to a strategy centered on the recognition that networks no longer maintain physical borders and on the possibility of building a protective fence around each individual user (or “thing”), allowing them to access their resources safely, from any place and device.
In the mesh, the user’s identity and its context thus become the “de fact” organizational perimeter, the ultimate control plane.
“Cybersecurity mesh is a customizable, scalable, flexible, and resilient approach that enables security controls to be extended to widely distributed assets by decoupling policy enforcement from the assets being protected.”
Gartner, Inc.
The above definition deserves special attention to detail. The mesh is customizable, scalable, flexible, and resilient because it allows defining and deploying ad-hoc combinations of controls for each user and each asset; add and remove controls on demand; and respond quickly to the dynamism of changes in protection requirements. Implicitly, it also raises the ability to centrally manage policies and apply them in a distributed manner.
Likewise, the execution of controls in the mesh uses multiple points of application of policies (“policy enforcement points” or PEPS) with the physiognomy of agents or “proxies”, which make it practically independent of the resources to be protected.
This feature results in control activities being carried out without delay, on any type of asset and location, just when they are needed.
Building the mesh “on-premise” in our own, data centers is possible, but it represents a limited and little-used option, especially in highly distributed contexts with significant geographic coverage.
The possibility of establishing a sufficient number of PEPS “close” to the total population of assets and of reducing latencies in response times appear as an insurmountable problem, among others.
Clearly, an “on-premise” network has more to do with providing palliative care to a terminally ill patient, the old perimeter of the network, than with dealing with the new realities and demands of our times.
At the other extreme, the public clouds of “security-as-a-service” providers appear to be the best alternative to reliably and conveniently deploy protective meshes of any size.
The scalability and accessibility of these types of actors allow them to host high-performance, resilient services, and ensure that their PEPS can be associated with an unlimited number of assets.
For too many years the world has been stubborn in collecting and operating a significant number of tools to face (with little success) the insatiable maelstrom of cyber threats.
A 2020 study by the renowned Ponemon Institute reveals that companies on average deploy more than 46 different technologies to protect themselves.
The net effect of this compulsive habit is, of course, the existence of insurance silos with a high cost of ownership; a limited, independent and selfish view of their environment; and minimal ability to interoperate with other pieces of this arsenal.
It should therefore come as no surprise that the holistic thinking of those who attack us manages to violate completely fragmented lines of defense.
Ubiquity is not the only distinguishing feature of the mesh. Gartner also highlights its potential as an integration vehicle to break down silos, enable security toolkits to work together, and bring a fully dynamic and collaborative ecosystem to life.
It is unrealistic to think, however, that the underlying intention is to integrate all the pieces and artifacts collected over time and plunge, once again, the technical teams into complex and uneven technological plumbing projects.
This statement becomes stronger if one considers that the current global trend is to consolidate providers and products into service platforms.
Apparently, the least rugged route to establish the corporate mesh is to select a primary supplier of the platform (but not the only one), and to integrate other “best of breed” products to it, in order to compensate for possible maturity gaps present. in the incumbent offer.
Measuring risks
Whichever path is chosen, it is essential to orchestrate a growing number of signals and risk indicators coming from different technological elements to make correct and timely decisions.
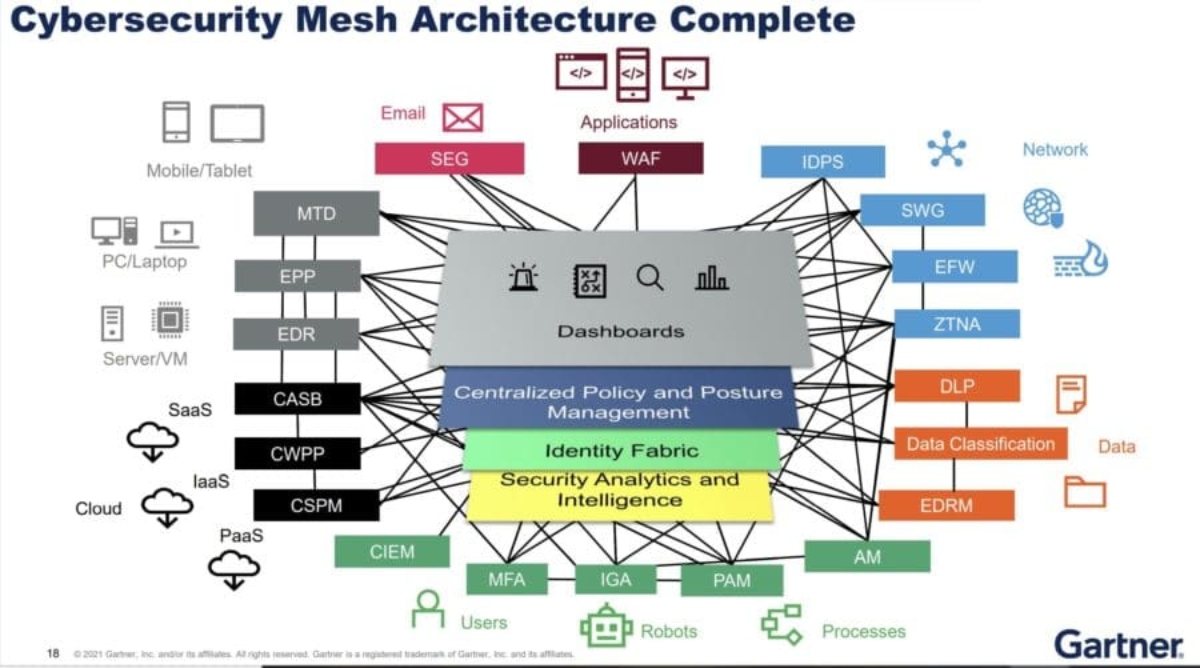
To do this, the mesh must offer four foundational layers that act as a force multiplier:
- Security Analytics and Intelligence: collect data from multiple security sources; conducts threat hunts; identifies, analyzes and prioritizes threats; and triggers orchestrated and automatic responses.
- Distributed Identity Fabric: it provides capabilities such as directory services, adaptive access, decentralized identity management, identity validation, and privilege management.
- Centralized Policy Management: you can translate a central policy into the native configurations of individual security tools and provide, as a more advanced alternative, dynamic authorization services at runtime.
- Consolidated Dashboard: offers a composite view of the security ecosystem, encouraging faster and more effective response from specialist teams to events and incidents.
Background of the mesh
The idea of a protective mesh is not new, and it is not completely innovative either.
It arises more out of necessity and rigorous analysis of the main collective currents in the world of business and technology. Zscaler, Inc., pioneer of security provided as a service from the cloud, inaugurates in 2008 the first global mesh.
Today Zscaler has more than 150 PEPs around the world and is the leading exponent of a converged market created by Gartner in 2019 under the name “Secure Access Service Edge (SASE)”.
It is safe to say that the preeminent members of the SASE segment make up the first generation of meshes and will, in the short term, play a starring role in subsequent evolutionary progressions.
Ecosystem giants such as IBM, Microsoft, Broadcom-Symantec, and McAfee will also seek to strike authority through acquisitions or the development of integrated offerings via unified XDR (Extended Detection and Response) platforms.
As is often the norm, only time and history will be able to judge whether cybersecurity meshes are the answer that a shocked and dangerous world has been demanding for many years.
Don’t miss Manuel Aceves’ talk in the conference program of the 7th America Digital Latin American Congress Business & Technology 2022 and visit his booth at the expo. Buy your tickets here
Noticias Recientes
- Gen participate in the 10th America Digital Latin American Congress 2025
- monday.com’s AI Vision: Unlocking Productivity for All
- Google Agentspace: Bringing AI agents and AI-powered search to enterprises
- Conected vehicules: how IoT is transforming the automotive industry
- Data vs. Creativity: R/GA challenges the myth
 Contact
Contact 

